What we do for your Business
The primary objective for a network penetration test is to identify exploitable vulnerabilities in networks, systems, hosts and network devices (ie: routers, switches) before hackers are able to discover and exploit them. Network penetration testing will reveal real-world opportunities for hackers to be able to compromise systems and networks in such a way that allows for unauthorized access to sensitive data or even take-over systems for malicious/non-business purposes.
15+
30
100%
4countries
Our penetration testing methodology includes an attack simulation carried out by our highly trained security consultants in an effort to:
- Identify security flaws present in the environment
- Understand the level of risk for your organization
- Help address and fix identified network security flaws
Ejaf technology Security network penetration testers have had experience supporting network, systems and hosts —not just trying to break them. They leverage this experience to zero in on critical issues and provide actionable remediation guidance.

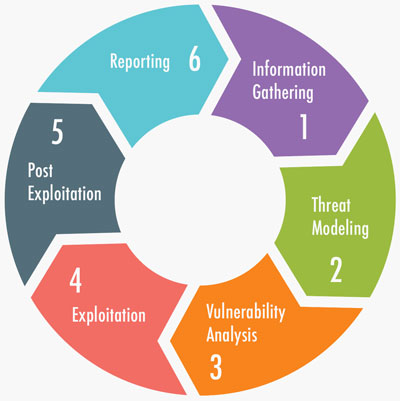
Each and every network penetration test is conducted consistently using globally accepted and industry standard frameworks. In order to ensure a sound and comprehensive penetration test, Ejaf technology leverages industry standard frameworks as a foundation for carrying out penetration tests. At a minimum, the underlying framework is based on the Penetration Testing Execution Standard (PTES) but goes beyond the initial framework itself.
At Ejaf technology Security, we consider the Delivery / Reporting phase to be the most important and we take great care to ensure we’ve communicated the value of our service and findings thoroughly. The deliverable consists of an electronic report that includes several key components including, but not limited to: Executive Summary, Scope, Findings, Evidence, Tools and Methodology. In addition to the report, a raw file in comma-separated value (CSV) format is also provided in an effort to optimize the remediation and management of any identified findings.